QueryVision offers both a Custom Authentication Provider toolkit for developers as well as a turnkey, out of the box relational provider.
Custom Authentication Provider for IBM Cognos
Our Custom Authentication Provider contains a rich set of documentation, tools, techniques, and full source code. A fully implemented relational authentication provider is also provided to jump start your Custom Authentication Provider Solution.
Snap in Relational Authentication Provider
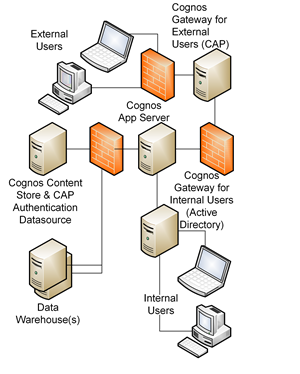
QueryVision’s “out of the box” solution uses a relational database as the authentication store and includes a companion Trusted Signon Provider for Single Sign-on support.
The product is optimized for Extranet or Intranet Applications. It also may be installed with its own schema or adapted to your existing relational security solutions in less than a day.
Databases supported:
- SQL Server 2000, 2005, 2008
- DB2 9.X
- Oracle 9g, 10g, 11g
Months vs. Days
The key benefit of our security solution is the reduction in both the risk and time required to develop a custom or relational authentication provider. Developing a provider from scratch is at least a 6 to 8 week effort. Furthermore, if this is done incorrectly, you risk compromising the security of your Cognos application.
Get Expert Advice
Our Toolkit comes with 2 days of training and consulting and our Relational Provider comes with free installation and configuration support, including advice on Cognos security does and don’ts. Alternatively, we can do it all for you and provide you with a full turnkey solution.
All The Missing Tools and Information
QueryVision’s Toolkit provides the key tools, techniques and documentation (class diagrams, security workflows, etc.) that are essential to being productive in developing an Authentication Solution. The documented relational implementation enables you to fully understand all the areas that need to be customized.
Adapt To Your Application Architecture Without Coding
Our snap-on Relational Provider and Toolkit implementations can be configured for different database schemas or database connectivity with simple configuration file properties.
Added Security Features
We provide the ability to encrypt database access credentials and user passwords for an extra layer of security. We also provide configurable logging support for both debugging and security access auditing.