QueryVision now supports the option for XSS checking in Cognos. This particular feature is used in highly secured intranet environments. However, getting this to work with external applications can be difficult. We will show you here how you can get this working with your applications when you run into URL rejection errors.
One of our large enterprise customers that was using Cognos 10.1 had to turn on the Cognos Application Firewall feature “Is third party XSS checking enabled?”. This can be found in Cognos Configuration as shown below, and is used to support drill-through with some extra security to prevent cross site scripting threats.
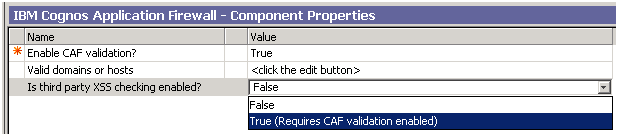
With this feature enabled, our application generated Cognos URLs were rejected with the following error:
CM-REQ-4158
 The search path “XSSSTARTstoreID(*27i6E85C03A59FF4D90ACB8EAAD060BA504*27)XSSEND” is invalid.
The search path “XSSSTARTstoreID(*27i6E85C03A59FF4D90ACB8EAAD060BA504*27)XSSEND” is invalid.
With XSS checking enabled, Cognos Connection generates different URLs. Custom applications that generate Cognos URLs are well advised to conform to the additional “xss encoding” in order to ensure that their URLs will be accepted by a Cognos installation with this feature enabled.
As to why Cognos has introduced this encoding the following knowledge base article provides the rationale:
http://www-01.ibm.com/support/docview.wss?uid=swg21339001
In a nutshell, with xss checking enabled, Cognos additional encodes any URL encoded aspects of their URLs, such as search paths, back urls, etc. with an additional level of encoding to ensure that web security applications such as SiteMinder will not flag Cognos URLs as representing a possible “cross site scripting” [or XSS] attack.
While the minimum that XSS requires is to avoid using [<], [>] or [‘] (single quote) in URLS, Cognos employs a more robust encoding which applies a general xss encoding algorithm which ensures that any possible characters outside letters or numbers will not cause cross scripting environments to reject valid Cognos URLs.
For any given query string parameter (e.g. &m_path=) or even the entire query string after “?”, do the following:
If the query string parameter is not already URL encoded, do URL encoding. Do NOT doubly URL encode.
Then, in the following order, replace the following characters:
- Replace “_” underscore with “_5f”
- Replace “*” star with “_2a”
- Replace “%” with “*”
- Replace [‘] single quote with “*27”
- Replace “+” standard URL encoding replacement for [space] with “*20”
- Append “XSSSTART” to the start of the string and “XSSEND” to the end of the string
For example, a search path such as:
/content/folder[@name=’Samples’]/folder[@name=’Models’]/package[@name=’GO Data Warehouse (analysis)’]/folder[@name=’Report Studio Report Samples’]/report[@name=’Employee Training by Year’]
becomes the following with URL encoding:
%2fcontent%2ffolder%5b%40name%3d%27Samples%27%5d%2ffolder%5b%40name%3d%27Models%27%5d
%2fpackage%5b%40name%3d%27GO%20Data%20Warehouse%20(analysis)%27%5d%2ffolder%5b%40name
%3d%27Report%20Studio%20Report%20Samples%27%5d%2freport%5b%40name%3d%27Employee
%20Training%20by%20Year%27%5d
becomes the following when Cognos xss encoding is applied (on top of the URL encoding):
XSSSTART*2fcontent*2ffolder*5b*40name*3d*27Samples*27*5d*2ffolder*5b*40name*3d
*27Models*27*5d*2fpackage*5b*40name*3d*27GO*20Data*20Warehouse*20(analysis)*27
*5d*2ffolder*5b*40name*3d*27Report*20Studio*20Report*20Samples*27*5d*2freport
*5b*40name*3d*27Employee*20Training*20by*20Year*27*5dXSSEND
A concrete example is when using this with a URL to use the default output.
Note that in this case both the &ui.object and &ui.backURL are xss encoded.
http://w23stdcg103/ibmcognos/cgi-bin/cognos.cgi?b_action=cognosViewer&ui.action=view
&ui.object=XSSSTARTdefaultOutput(*2fcontent*2ffolder*5b*40name*3d*27Samples*27
*5d*2ffolder*5b*40name*3d*27Models*27*5d*2fpackage*5b*40name*3d*27GO*20Data
*20Warehouse*20(analysis)*27*5d*2ffolder*5b*40name*3d*27Report*20Studio
*20Report*20Samples*27*5d*2freport*5b*40name*3d*27Employee*20Training*20by*20Year
*27*5d)XSSEND&ui.name=XSSSTARTEmployee*20Training*20by*20YearXSSEND
&ui.format=PDF
&ui.backURL=XSSSTART*2fibmcognos*2fcgi-bin*2fcognos.cgi*3fb_5faction
*3dxts.run*26m*3dportal*2fcc.xts*26m_5ffolder
*3diDA7AE2CE9F2140E7A8A82F3B1DB3CFF8XSSEND
It is important to note that the xss encoding is NOT accepted by the Cognos server if xss checking is not enabled.
